The official Microsoft documentation (link) recommends deploying the connection scripts as packages, but I thought that it would be fancy to deploy them as applications – because the application model is more powerful and offers several features that can’t be achieved with packages.
TL;DR:
Device Tunnel (details)
1. Create the application which runs the configuration script: powershell.exe -ExecutionPolicy Bypass -File ".\DeviceTunnel_installer.ps1"
2. Detection method: PowerShell script, Get-VPNConnection -AllUserConnection "DEVICE TUNNEL" -ErrorAction SilentlyContinue
3. User Experience: Install for system; Whether or not a user is logged on; Minimized
4. Requirement: Only Windows 10
Deploy the application to a device collection.
User Tunnel (details)
1. Create the application which runs the configuration script: powershell.exe -ExecutionPolicy Bypass -File ".\UserTunnel_installer.ps1"
2. Detection method: PowerShell script,Get-VPNConnection "USER TUNNEL" -ErrorAction SilentlyContinue
3. User Experience: Install for system; Only when a user is logged on; Minimized
4. Requirement: Only Windows 10
Deploy the application to a user collection.
Notice that the user experience is set to “Install for system”, but the application is deployed to a User collection. Based on my testing, it causes the program to run in SYSTEM context (admin rights!), but the detection method runs in the current user context (which is good in our case – and bad if you were trying to write a detection script which requires admin rights…).
Cheat: Scoped User Tunnel deployment (eg. notebooks only) (details)
If you want to limit the deployment of the User Tunnel to only selected devices, here is a workaround:
1. Create another application which creates a registry key, eg.:
HKEY_LOCAL_MACHINE\Software\AOVPN\UserTunnelDeploymentEnabled (DWORD) = 1
2. Configure this application as a dependency for the User Tunnel application with automatic install disabled
3. Deploy this application to those devices on which you want to enable the User Tunnel deployment
Extended edition
Device Tunnel
In the following steps I’m creating an application which configures an AlwaysOn VPN device tunnel, named F12_AOVPNDevice.
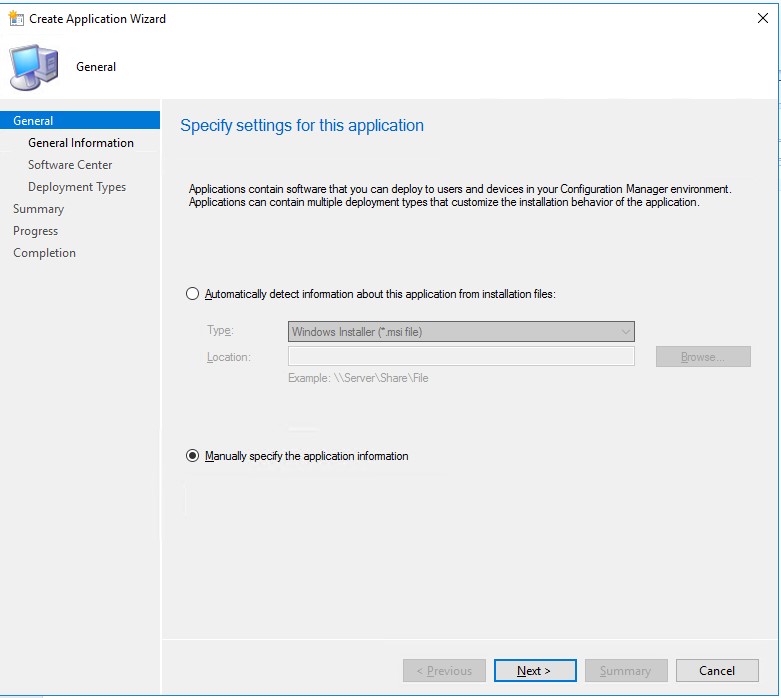
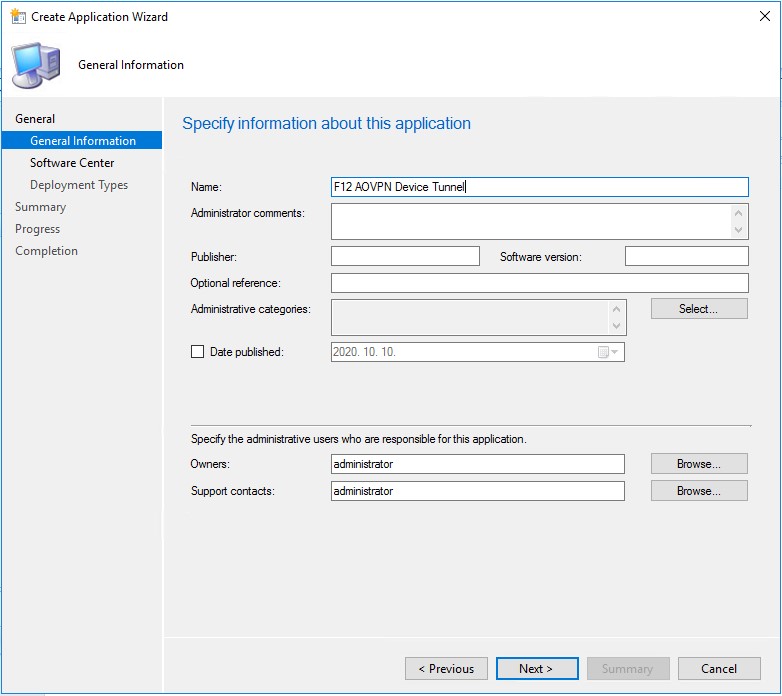

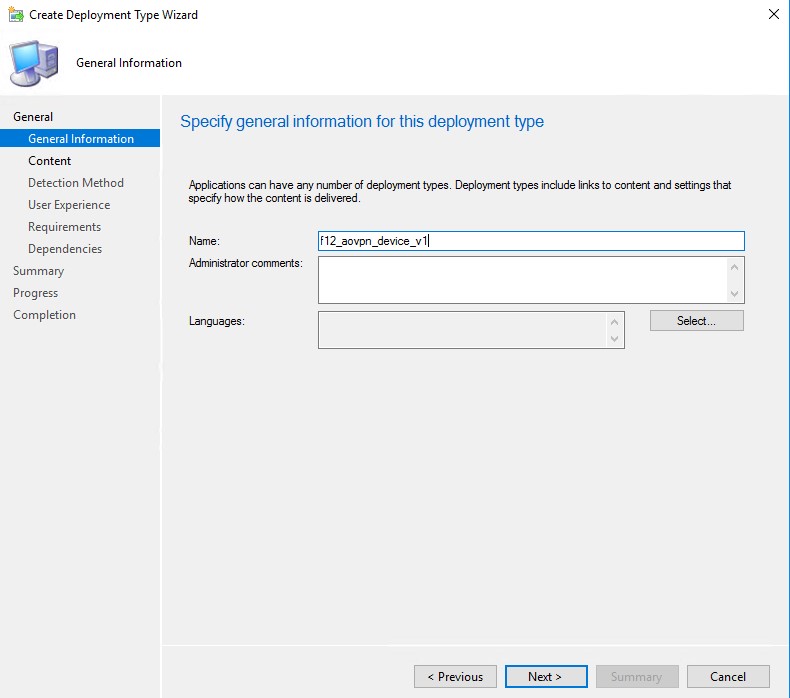
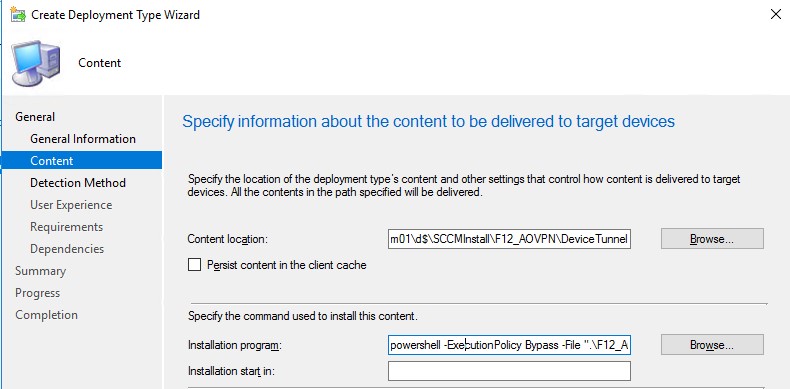
On the Content page, browse for the folder where the script can be found. The following installation program is specified in my case:
powershell -ExecutionPolicy Bypass -File ".\F12_AOVPN_D1.ps1"
The application detection method will be a PowerShell script, with the following content:Get-VPNConnection -AllUserConnection "F12_AOVPNDevice" -ErrorAction SilentlyContinue
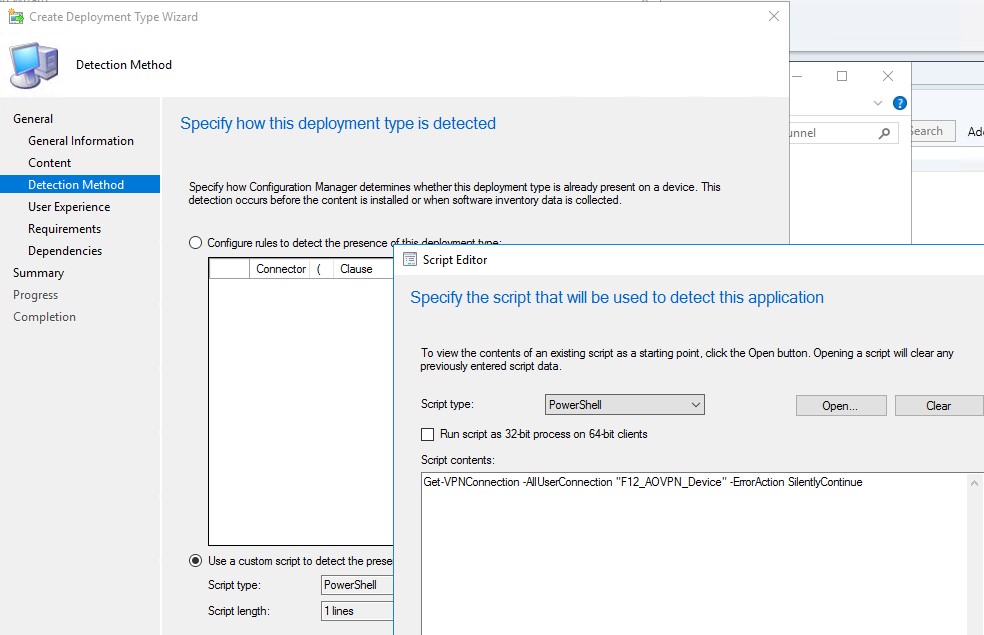
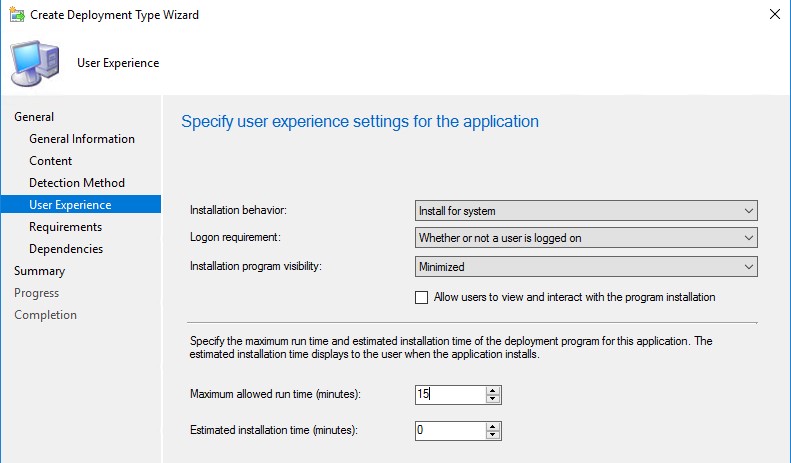
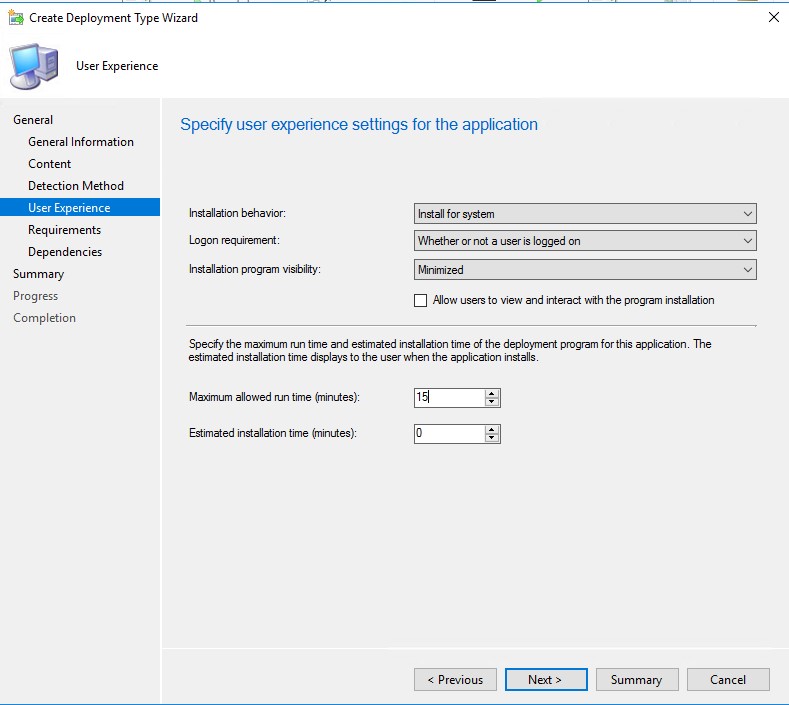
On the User Experience tab, configure the settings as follows:
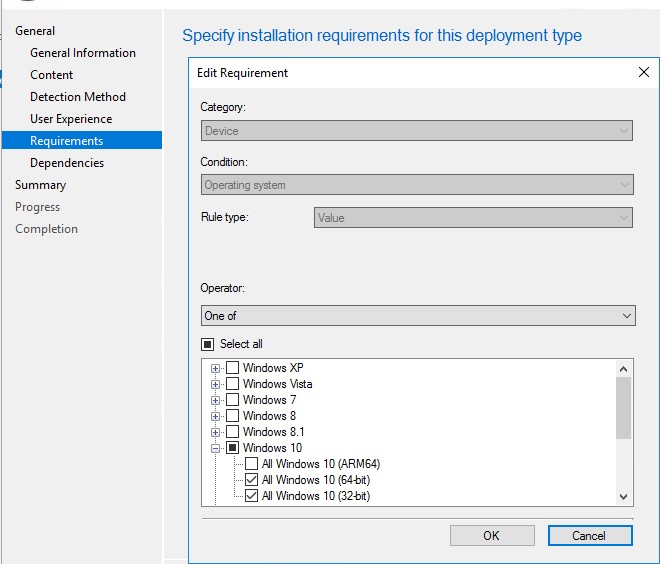
On the Requirements page, one requirement will be specified: only Windows 10 (32/64 bits) operating systems are required:
The process is straightforward from this point. After creating the application, deploy it to the device collection. For testing purposes, I deployed it as Available:
After successful installation, the VPN connection can be verified several ways – I chose PowerShell:
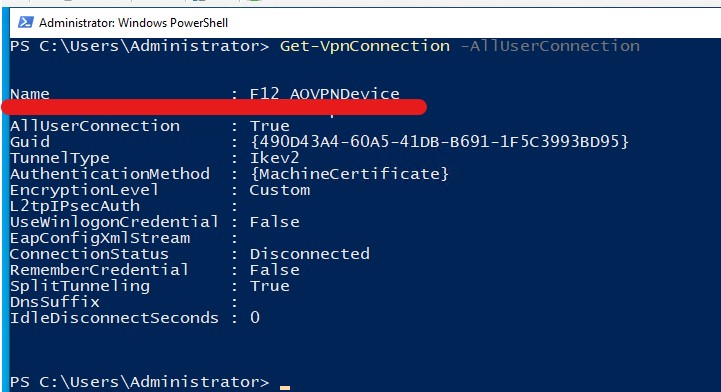
User Tunnel
Deploying the user tunnel is almost the same, although there are some aspects to consider:
– If the application was successfully installed for a user on the computer, it may take some time for another user on the same machine (The next Application Deployment Evaluation cycle + User Policy Evaluation Cycle). Microsoft’s approach (deploy the package once for every user who logs on) is better in other ways: the profile will be installed immediately for users logging on for the first time; there is no need to evaluate user policies; etc.
– Deploying the application to a User Collection means that users will receive the VPN profile anywhere they log on – even on their PCs that doesn’t need it (cheat below).
– The detection method is only looking for a VPN connection with a particular name – make sure that this name is unique, or fine tune the detection method to check the server address too…
So let’s start:

Everything almost the same so far. I forgot to take screenshot of the Content page, but you can see my settings on the Summary screenshot below.
On the Detection Method page, the PowerShell script is a bit different:Get-VPNConnection "F12_AOVPN_User" -ErrorAction SilentlyContinue
There is no -AllUserConnection parameter, because user tunnels are user specific.

On User Experience page, choose “Install for system” as installation behavior, so the script will run in SYSTEM context. The logon requirement should be set to “Only when a user is logged on”. I’m not sure if RDP sessions (or Hyper-V enhanced sessions) satisfy this criteria, but keep in mind that console sessions are required.
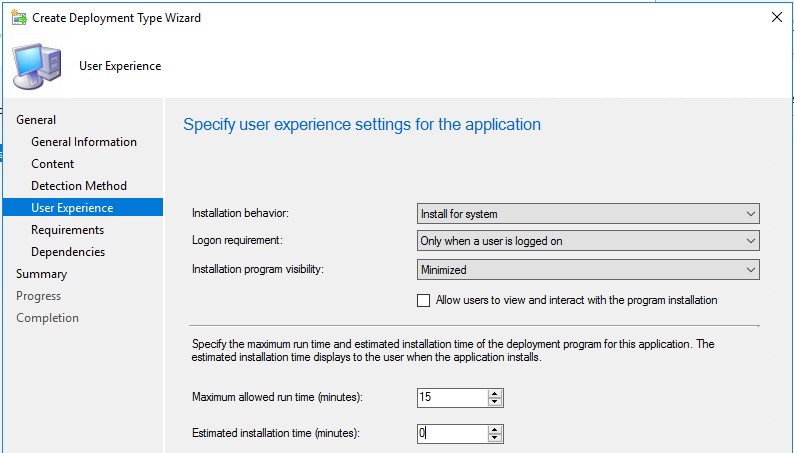
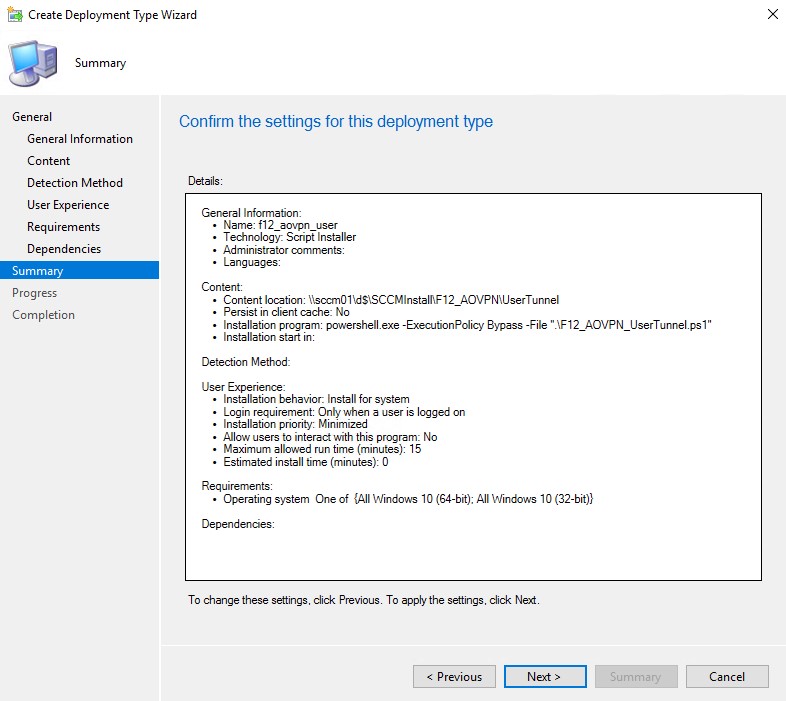
Now everything is ready, the application can be deployed to a user collection.
Cheat: Scoped User Tunnel deployment
If you want to restrict the user tunnel deployment to certain computers, there can be some standard ways (SCCM Global Conditions?) or uncommon solutions like this.
Before moving to this solution, consider the official Microsoft recommended deployment method (package for every user who logs on) as this can be deployed to device collections too. The only disadvantage is that anybody logging on the computer will receive this setting – but keep in mind that User Tunnel connection request are handled by NPS – so even if a not intended user receives the VPN settings, the connection won’t establish.
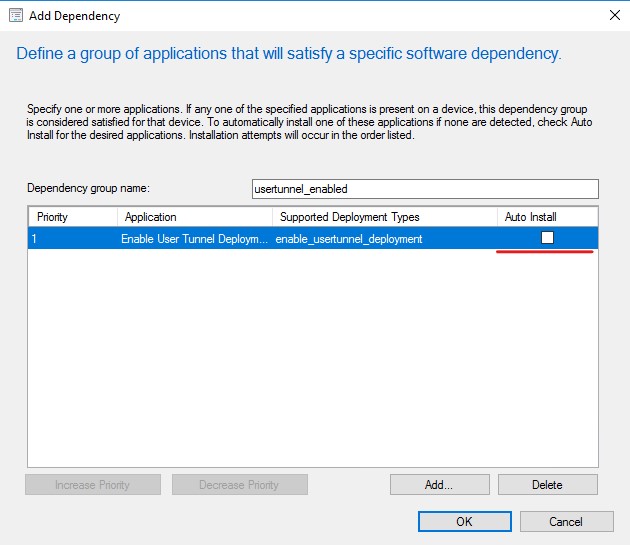
So the idea behind this workaround is to create a registry key on the target system to determine if User Tunnels can be deployed. The registry configuration is a separate SCCM application which can be used as a dependency for the User Tunnel application… not too elegant, but it works.
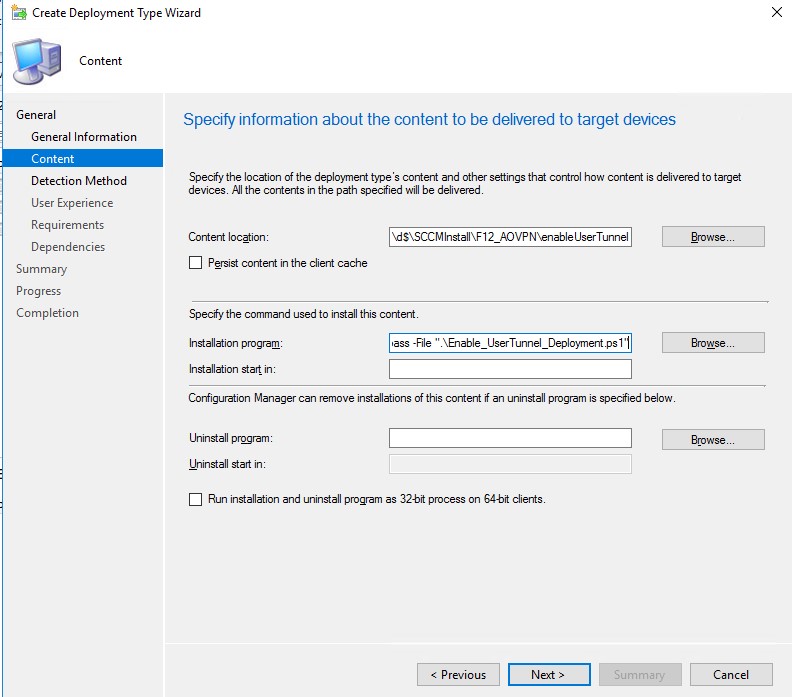
Create a separate application (Enable User Tunnel) with the following deployment type:
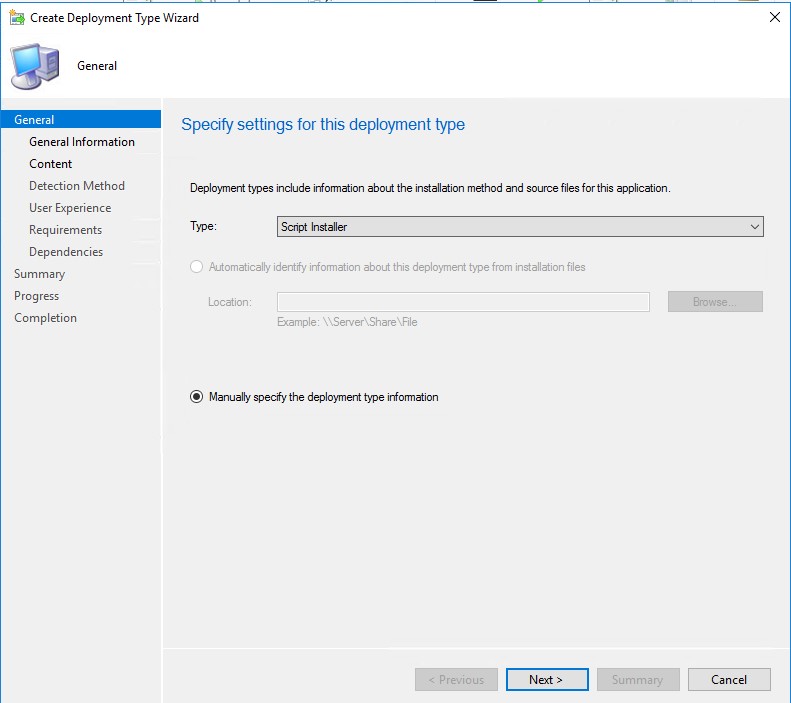
On Content page speficy the source directory and the installation programpowershell.exe -executionpolicy bypass -File ".\Enable_UserTunnel_Deployment.ps1"
Enable_UserTunnel_Deployment.ps1 content:$key = 'registry::HKEY_LOCAL_MACHINE\SOFTWARE\F12_AOVPN'
$property = "UserTunnelDeploymentEnabled"
$value = 1
if (!(Test-Path $key)){New-Item -Path $key >> $null}
New-ItemProperty -Path $key -Name $property -PropertyType DWORD -Value $value -Force >> $null
The Detection method will consist of checking the registry setting:
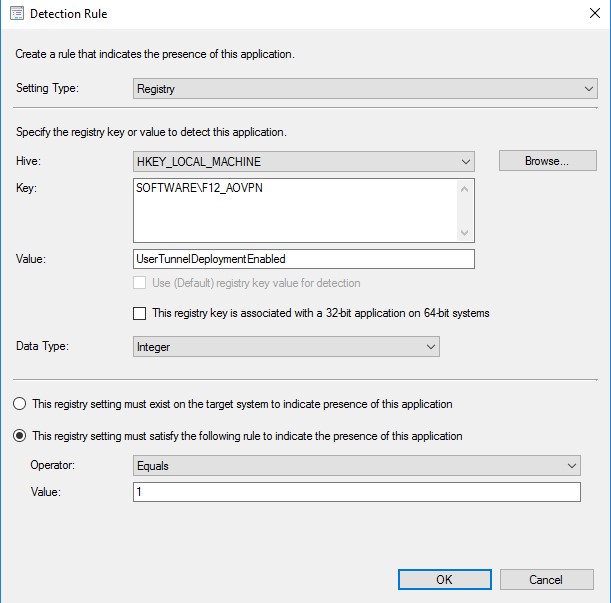
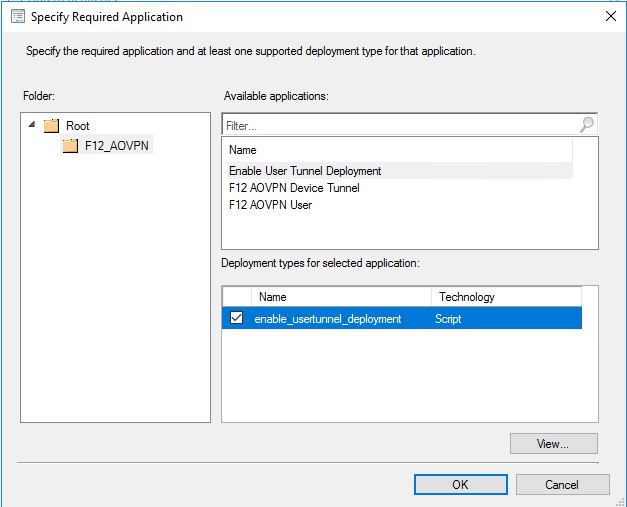
After creating the application, modify the User Tunnel application so it will have this deployment type as a dependency. Navigate to the Dependencies tab of the deployment type and click on “Add..” and select this new application as dependency:
Make sure you unchecked the Auto Install box.
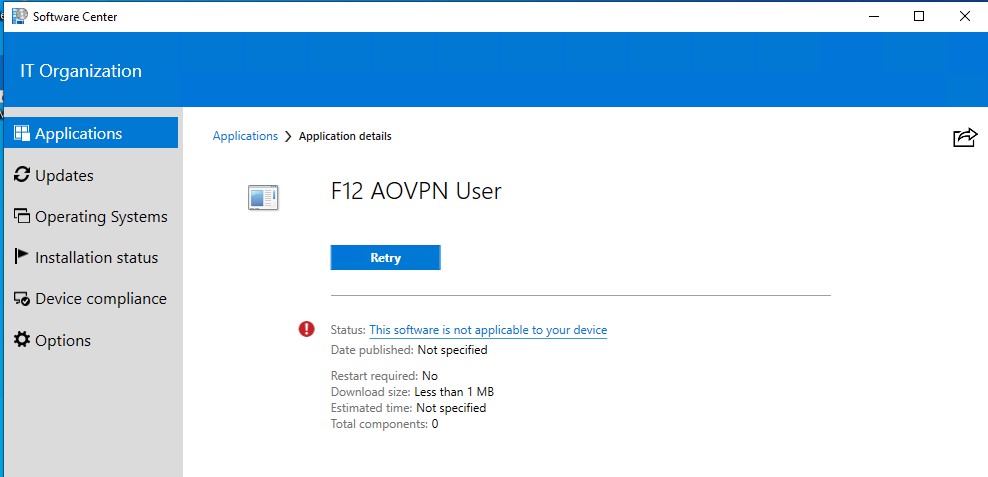
The next step is to deploy “Enable User Tunnel Deployment” application to those devices on which you want to enable user tunnel deployment. On those devices where this application is not installed, Software Center will not install the user tunnel with the following status: “This software is not applicable to your device”
Now I install the application on the computer:
After some time you can retry the installation of the user tunnel:


