Recently, I was scripting an Azure App registration workflow and had some headaches figuring out how to grant admin consent to the application with PowerShell. Actually, if AzureCLI is installed you can use the following command:
az ad app permission admin-consent --id <application id>
However, I wanted to find some native PowerShell-way to solve this problem and this is how I came accross this solution. So this script is basically giving some context to the answer provided by Kitwradr.
TL;DR
- Ensure you have AzureRM Powershell module installed
- Modify the $appName variable’s value accordingly
- When prompted, enter tenant admin credentials
Script:
$appName = "<AppDisplayName>"
Login-AzureRmAccount
$context = Get-AzureRmContext
$tenantId = $context.Tenant.Id
$token = [Microsoft.Azure.Commands.Common.Authentication.AzureSession]::Instance.AuthenticationFactory.Authenticate($context.Account, $context.Environment, $TenantId, $null, "Never", $null, "74658136-14ec-4630-ad9b-26e160ff0fc6")
$headers = @{
'Authorization' = 'Bearer ' + $token.AccessToken
'X-Requested-With'= 'XMLHttpRequest'
'x-ms-client-request-id'= [guid]::NewGuid()
'x-ms-correlation-id' = [guid]::NewGuid()}
$azureApp = Get-AzureRmADApplication -DisplayName $appName
$azureAppId = $azureApp.ApplicationId
$url = "https://main.iam.ad.ext.azure.com/api/RegisteredApplications/$azureAppId/Consent?onBehalfOfAll=true"
Invoke-RestMethod -Uri $url -Headers $headers -Method POST -ErrorAction Stop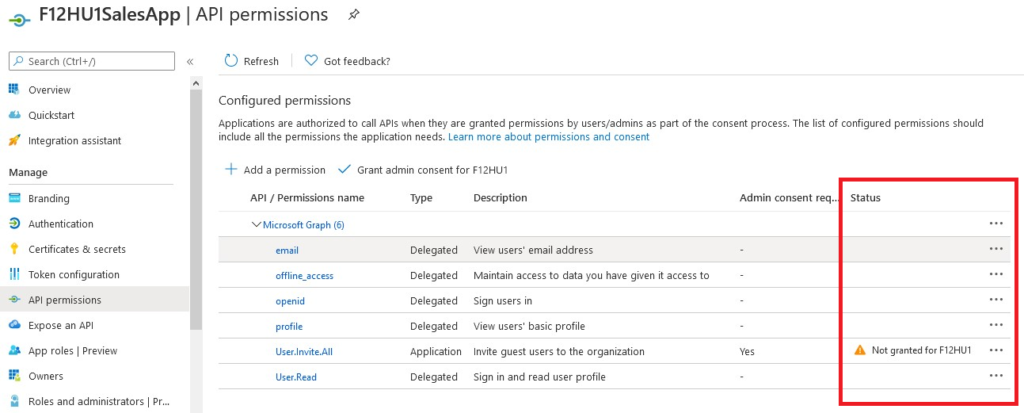
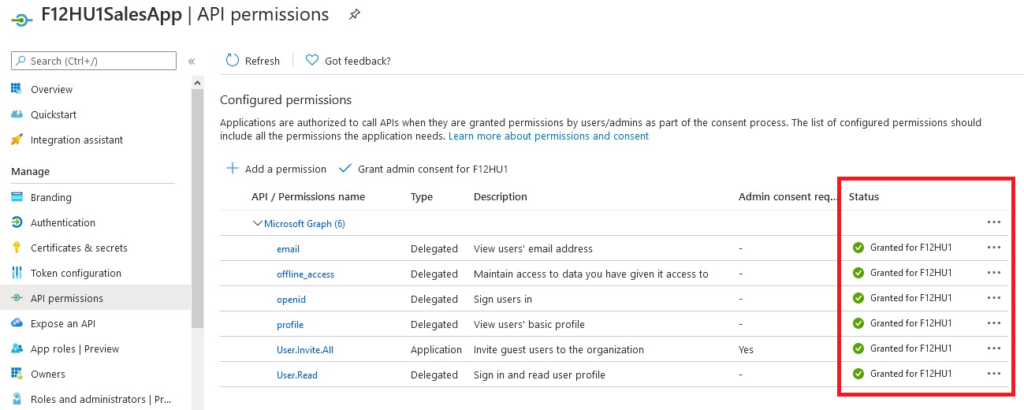
Enjoy 🙂
