I’m really into this Windows Hello for Business topic… Recently, I was going through the “RDP with WHfB” guide from MS Learn (link) which gave me an idea: can this method be used to protect user VPN certificates? The short answer is: yes, but no 🙂
TL;DR
– Depending on your current infrastructure, several options are available to protect VPN with MFA: Azure MFA NPS extension, SAML-auth VPN with Conditional Access, Entra ‘mini-CA’ Conditional Access
– Hello for Business can be used to protect access to certificates, why not use it to protect VPN certs?
Protecting VPN with MFA with Microsoft tools
NPS Extension
The most popular option I know to protect VPN with MFA is the Azure MFA NPS extension (link). The logic is very simple: the RADIUS request coming to the NPS server is authenticated against Active Directory, then the NPS extension is doing a secondary authentication (Azure MFA).
SAML-based authentication with Conditional Access
This depends on the vendor of the VPN appliance, but the mechanism is that an Enterprise application is created in Entra and Conditional Access policy can be applied to it.
Conditional Access VPN
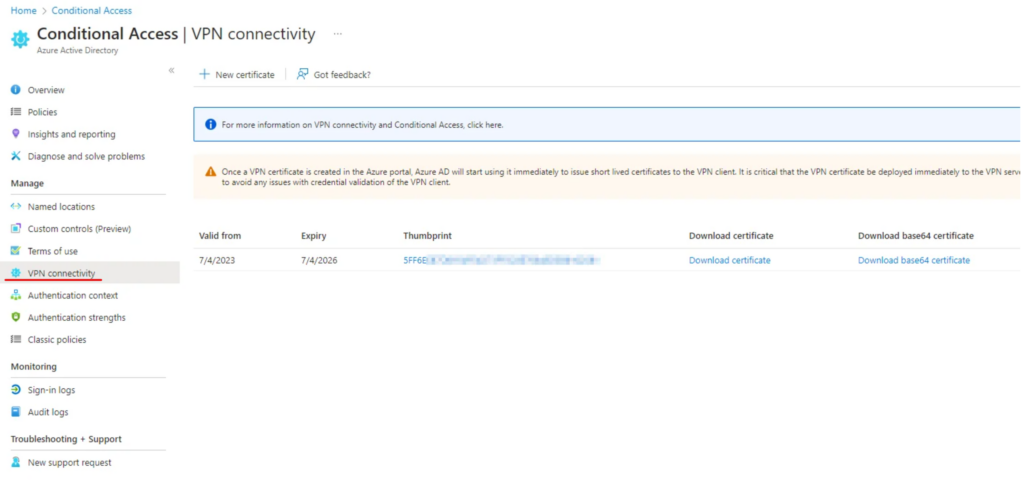
There is another option which is called “Conditional Access VPN connectivity” in Entra – and by the way it seems to me that Microsoft is hiding this option (I guess it’s because it is using Azure Active Directory Graph which is deprecated). I found a photo how it looked like in the old days (picture taken from here):
In the Entra portal this option is not visible (at least for me):
But when using the search bar, the menu can be found:
Some documentation links about this feature:
- Conditional Access Framework and Device Compliance for VPN (link)
- Conditional access for VPN connectivity using Microsoft Entra ID (link)
- VPN and conditional access (link)
The mechanism in short: Entra creates a ‘mini-CA’ which issues a short-lived certificates to clients; when a Windows VPN client is configured to use DeviceCompliance flow, the client attempts to get a certificate from Entra before connecting to the VPN endpoint (from an admin standpoint a ‘VPN Server’ application is created in Entra and conditional access policies can be applied to this application – I’m not going into details about this one, mainly because I encountered a lot of inconsitencies in the user experience when testing this solution 🙃) – and when everything is OK, the user gets a short-lived certificate which can be used for authentication (eg. EAP-TLS)
Some screenshots about this:
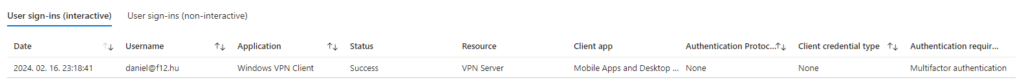
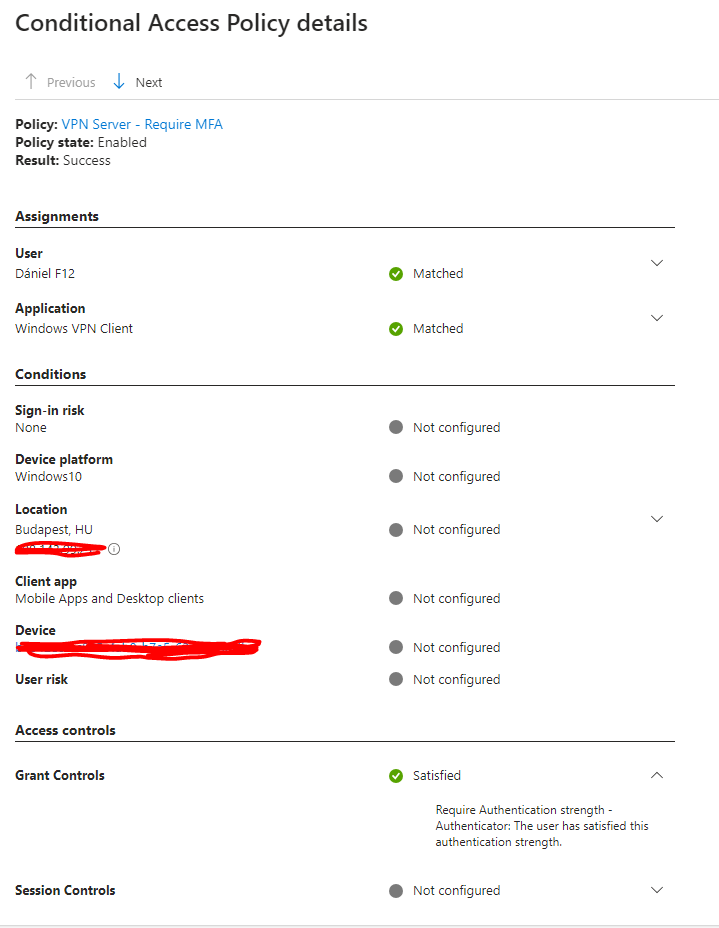
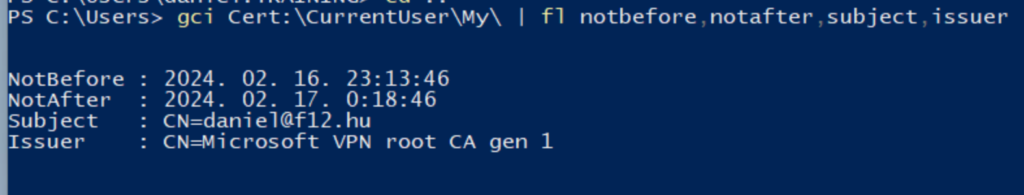
VPN Certificate created with Microsoft Passport KSP
Disclaimer: it is not an official/supported by Microsoft method to use VPN certificates for authentication, I tested it only for entertainment purposes.
This was the initial trigger of this post – based on the “Remote Desktop sign-in with Windows Hello for Business” tutorial, create VPN certificates using the Microsoft Passport KSP (link). The process is straigthforward:
– create the VPN certificate template (or duplicate the one you already have)
– export the template to a txt file
– modify the pKIDefaultCSPs setting to Microsoft Passport Key Storage Provider
– update the template with the new setting
User experience: well, if the user is WHfB enrolled and logs in with WHfB then nothing changes (the certificate is used “silently” upon connecting) – but when using password to log in to Windows, the VPN connection prompts for Hello credentials:
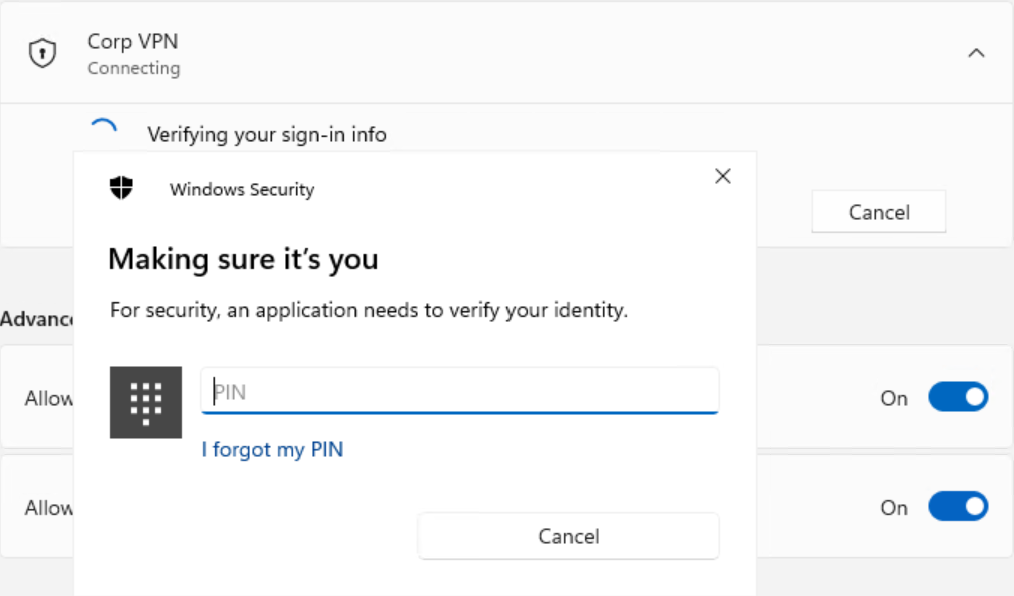
So if Hello for Business can be considered a multi-factor authentication method, then this solution fits as well 🙂
