Scenario: the business is now convinced that computers should be managed centrally (either with Active Directory or Azure Active Directory) instead of having WORKGROUP computers.
Problem: after joining to (Azure)AD, users will have a new profile created. Gone are their settings, wallpaper, pinned icons, etc. You need to note these settings, copy the files to the new profile and so on.
After searching the net you may come across 3rd party solutions to address this headache – or decide to find some Microsoft way to do this.
The “don’t do that” solution: use the Win32_UserProfile class’ ChangeOwner method (link).
Why: several settings are tied to cached credentials (these should be entered again), some icon pinnings on the taskbar will lose, but the worst thing is that some settings may be tied to a personal account that should be migrated to the work account (user is logged in to a personal Microsoft account, OneDrive is syncing business data to personal OneDrive, etc.) – with a lift-and-shift approach, these settings will remain in place and this should be avoided.
DISCLAIMER: I’m just sharing this “don’t do that” tutorial just in case someone has the same idea that Win32_UserProfile.ChangeOwner is a good solution. If you considered the above and still want to give it a try, do this on your own risk. There are tools available to accelerate the process developed or recommended by Microsoft (USMT or PCmover Express [link])
So what I did after AzureAD joining the computer was to log in with the AzureAD account of the user and noted the profile path for both the personal account and the corporate account. Login created the local profile, but since the Win32_UserProfile.ChangeOwner method fails if the source or the target profile is loaded, another admin is required to perform the changes. So I logged in with a Global Administrator (the two accounts logged off), then launched PowerShell (as admin) – or you can configure additional administrators [link].
gwmi -query "select * from Win32_UserProfile" | ft localpath,sid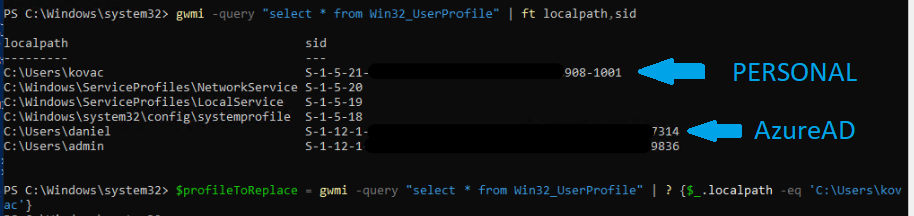
Next was to store the personal profile in a variable:
$profileToReplace = gwmi -query "select * from Win32_UserProfile" | ? {$_.localpath -eq 'C:\Users\kovac'}Then call the ChangeOwner method:
$profileToReplace.ChangeOwner('<sid of AzureAD profile>', 1)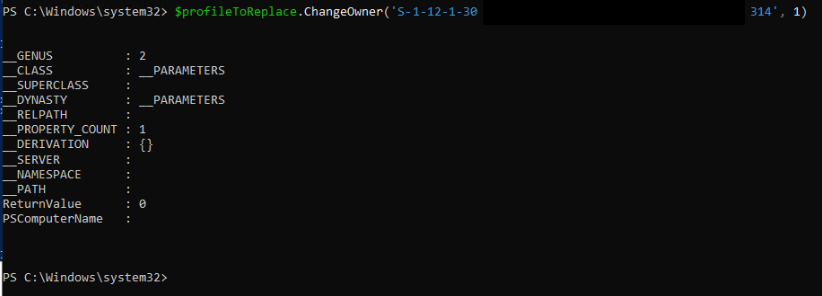
Now when the user logs on using AzureAD credentials, the old profile is loaded with almost all settings… Almost. First welcome message:
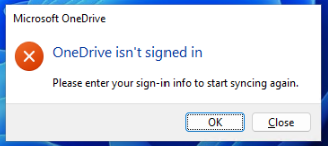
The same applies to Edge/Chrome profile. Another inconvenience I noticed is that pages pinned by Edge to taskbar are missing their icons:
The login screen still shows the personal profile (if the users logs in a new local profile will be created). This entry can be removed with netplwiz:
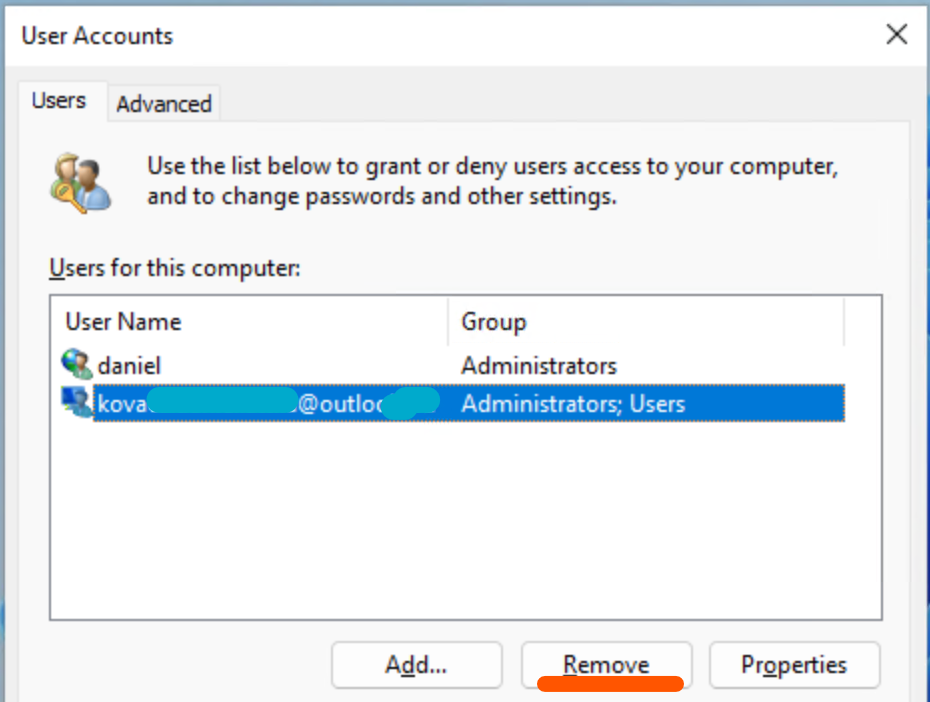
And at this point I realized that lot of settings can be tied to a personal cloud account which you may not want to migrate to the business profile – so I didn’t go further, but wanted to share my experiences so that you can learn from my mistake 🙂
