The Edge Drop is a really wonderful feature, but my inner data protection officer was bugging me to investigate if it is safe in an enterprise (or SMB) environment. There are several options to protect corporate data (labels, App Protection Policy, DLP policies, etc.) but not every business is lucky enough to afford the required licenses or to implement all these funcitionalities. Anyways, the goal of this post is to raise awareness and a call for action to evaluate the current policies with Edge’s Drop feature in focus.
TL;DR
– Edge’s Drop feature’s impact depends on the current policies and needs
– SharePoint access control policies don’t protect against Drop
– You may want to disable Drop, even if it is currently limited to Windows/macOS
What is Edge Drop?
It’s is actually a chat with yourself with the option to share files (MS doc). Files are stored in the user’s OneDrive for Business “Microsoft Edge Drop Files” folder. All you need to do is to log in to the Edge browser and it is ready to use (first time use will need 1-2 minutes to set up).
Problem statement
From the AzureAD perspective, this action is actually a sign-in to the “Microsoft Edge” application. If you have policies targeting the “Office 365 SharePoint Online” application (eg. policies created by SharePoint admin center’s Unmanaged devices access control setting) or “Office 365” application these policies may not apply. This can lead to accidental data loss.
In the following scenarios, the primary principal is that cloud content should be accessible only on managed devices (Hybrid AzureAD joined or compliant) – other devices are blocked (or restricted to view-only web access).
Scenario1
SharePoint admin center – Policies – Access control – Unmanaged devices = Allow limited, web-only access
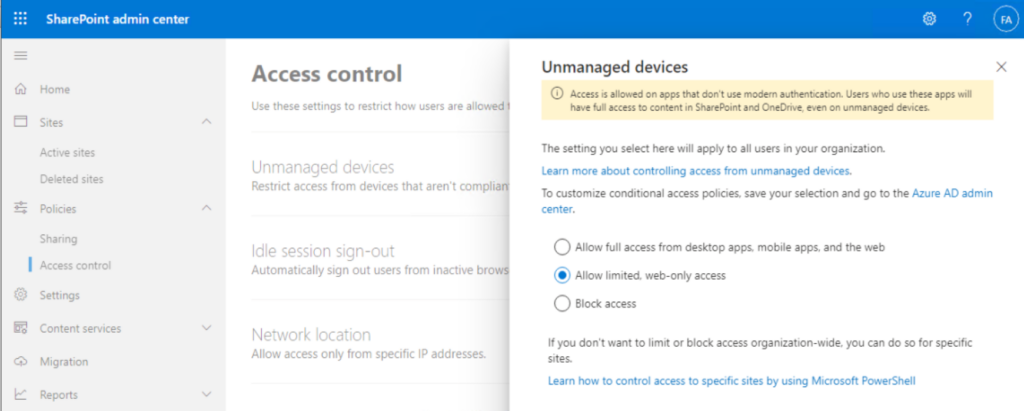
This setting creates two Conditional Access policies:
1. [SharePoint admin center]Block access from apps on unmanaged devices
Office 365 SharePoint Online app, Client app = Mobile apps and desktop client as condition, Require device to be marked as compliant or Require Hybrid Azure AD joined device as Grant control
2. [SharePoint admin center]Use app-enforced Restrictions for browser access
Office 365 SharePoint Online app, Client app = Browser as condition, Use app enforced restrictions as session control
Experience on a non corporate device, user is logged in to Edge:
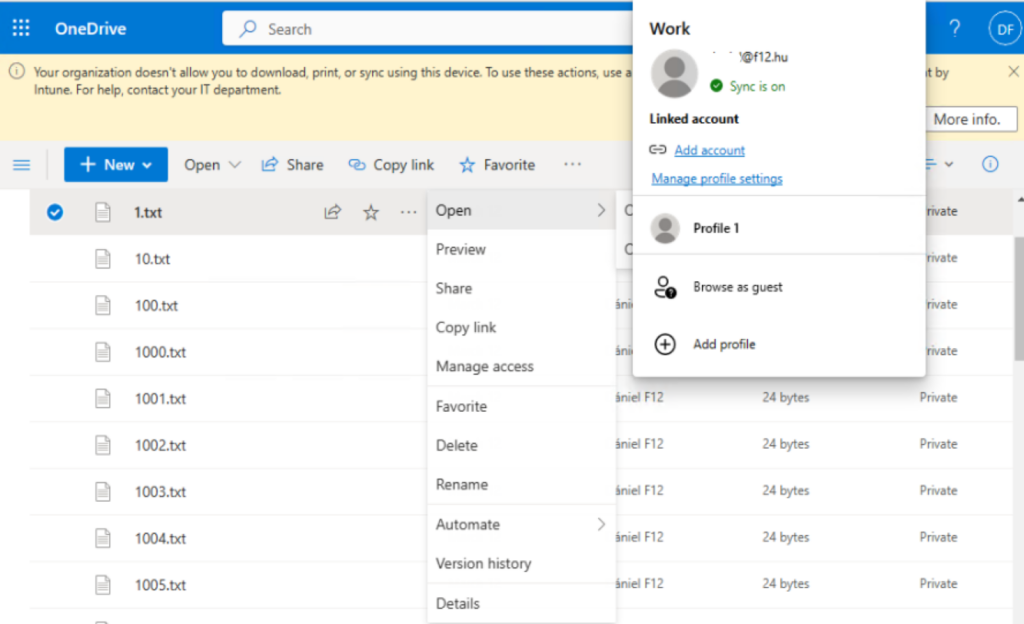
As you can see, there is a warning message that files can’t be downloaded and there is no download option in OneDrive. Let’s see if Drop allows downloading:
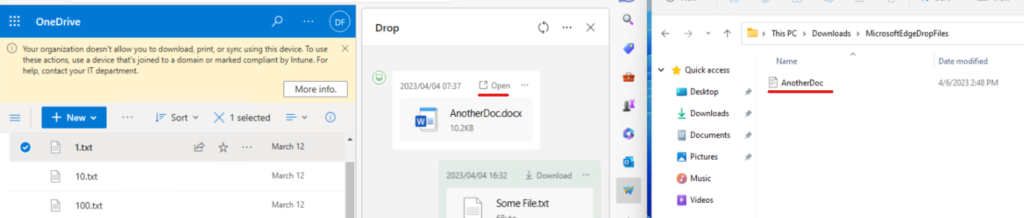
Yes, it does… too bad.
Scenario2
SharePoint admin center – Policies – Access control – Unmanaged devices = Block access
This option generates one Conditional Access policy:
[SharePoint admin center]Use app-enforced Restrictions for browser access
Office 365 SharePoint Online app, Client app = Browser as condition, Use app enforced restrictions as session control
Experience on a non corporate device, user is logged in to Edge:
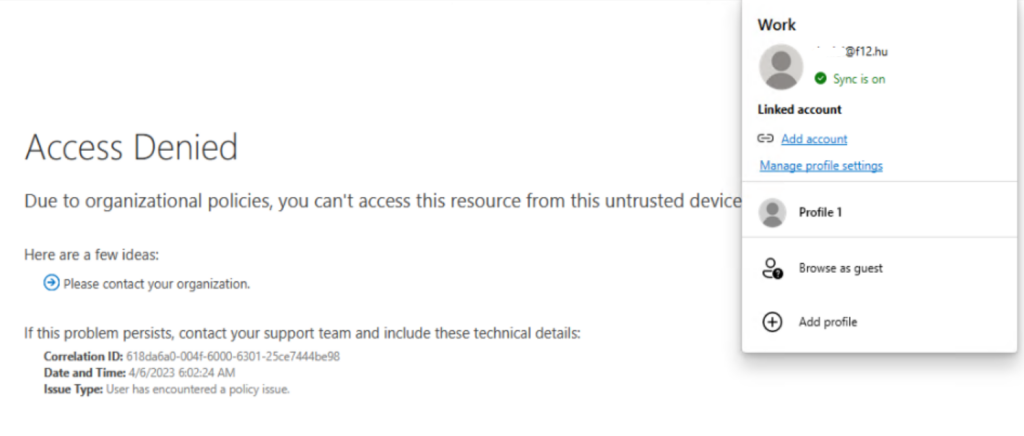
As you can see, OneDrive can’t be opened from the browser. Let’s see if Drop is dropped 🙂
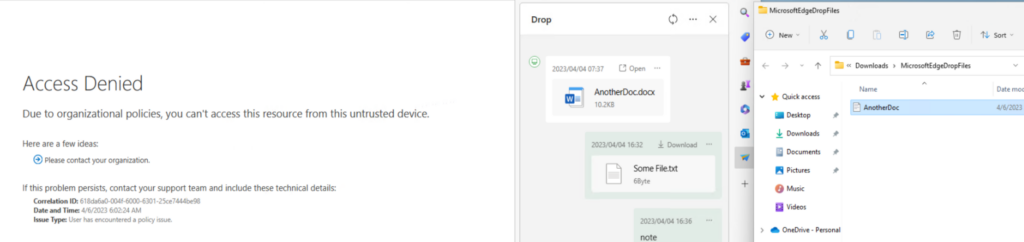
Not really…
Scenario3
Conditional Access Policy – Office365 – Require device to be marked as compliant or Require Hybrid Azure AD joined device as Grant control
The purpose of this demo policy is to restrict every Office 365 resource to managed devices (including OneDrive). This is a more restrictive policy, needs a lot of planning and testing before implementing – but I hope it will prevent Drop from downloading files on unmanaged devices.
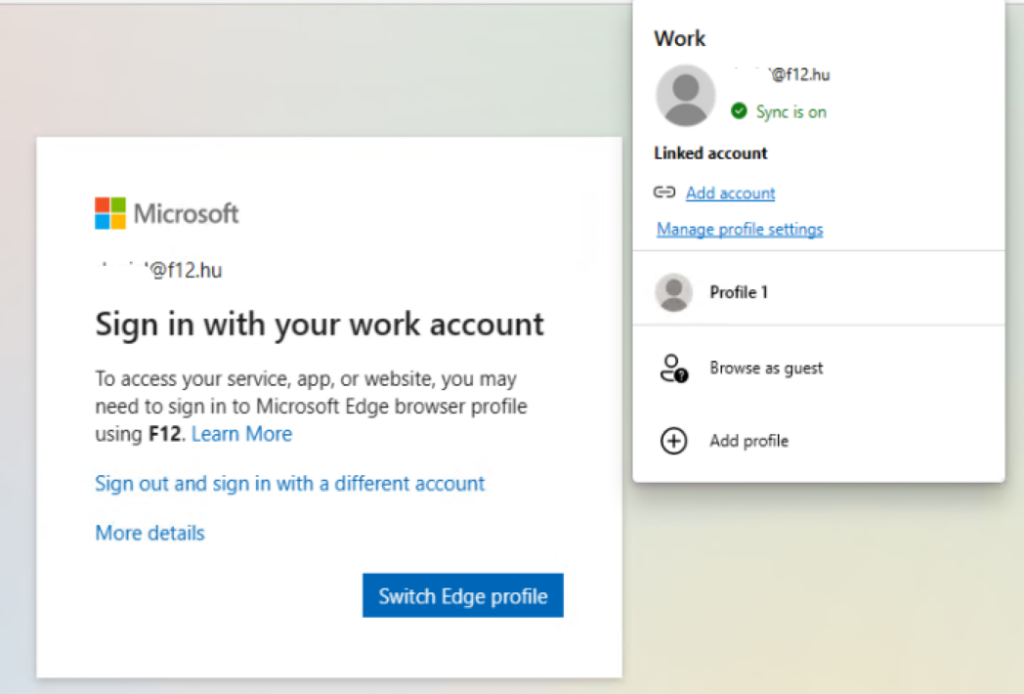
Experience: if I do not register the device, it keeps asking me to log in:
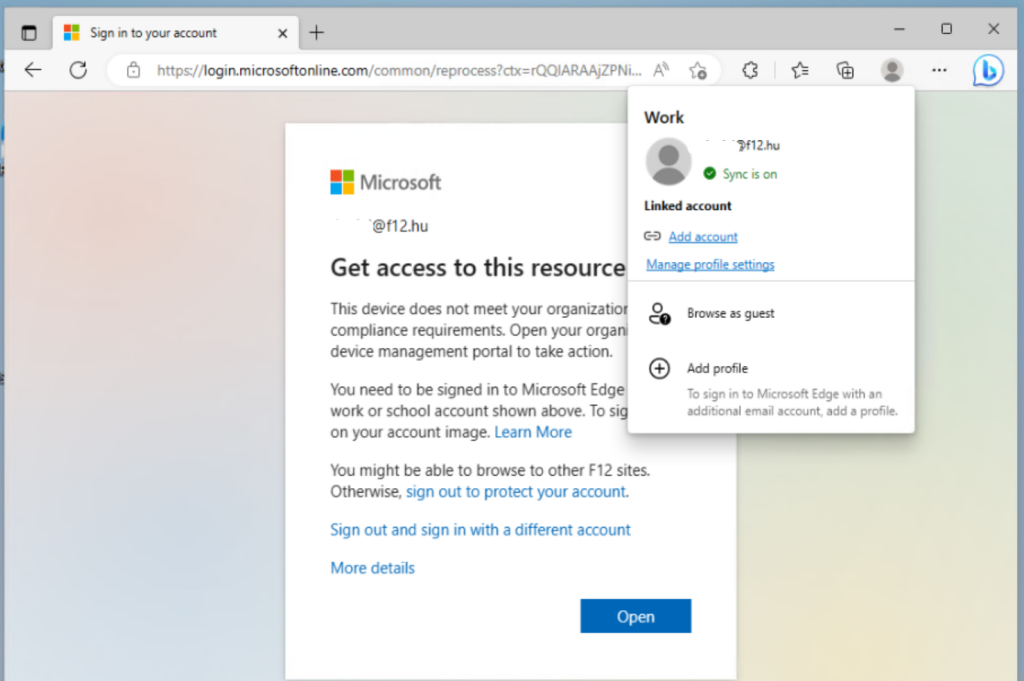
When I register the device, access is blocked:
How about Drop? This time it is stuck in Initializing, files can’t be downloaded (same experience when device is not registered):
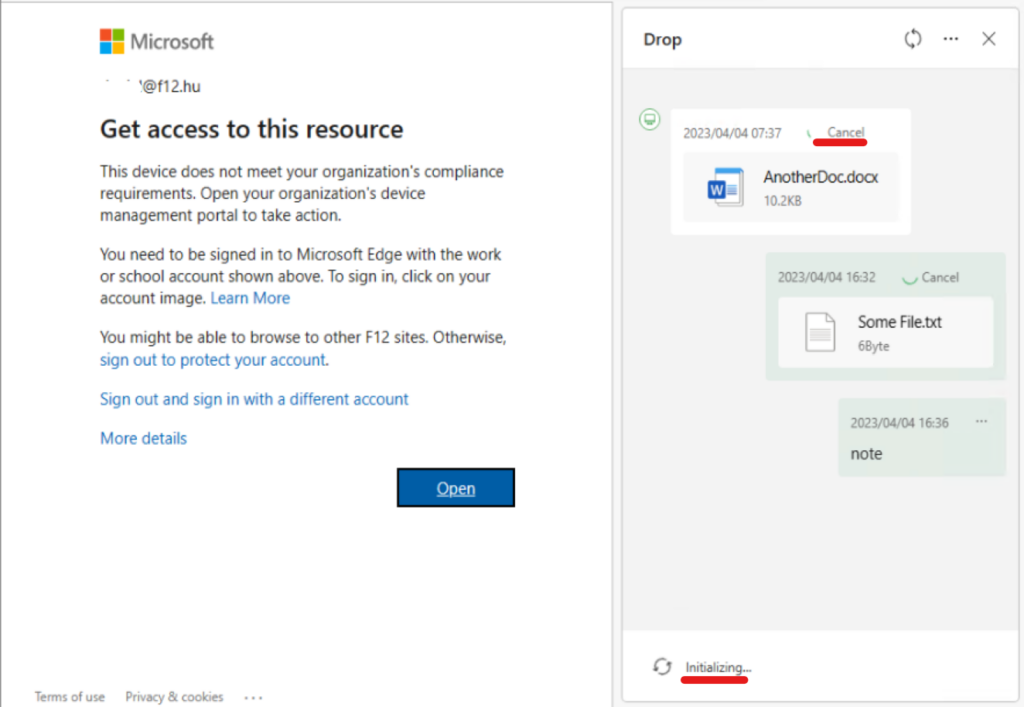
Okay, this policy does the trick but it has large impact on users.
A less painful solution is to disable Drop on managed devices (link), so users won’t be able to upload files from corporate devices. This can be done via Group Policy or Intune configuration profile. However, the setting is only supported on Windows and macOS devices, so users will not be prevented from uploading via Drop on iOS/Android devices.
Conclusion: several other scenarios are possible and several tools are available to prevent accidental data leak, which will not be covered in this post because it aims only to raise awareness, make you review your security settings when new features are available in your tenant.
