Back in the days, I wrote about the Entra Workload Identities Premium licence and it’s very appealing capabilities (link). One of my favorites was the defaultAppManagementPolicy which can (also) restrict the lifetime of (new) password credentials created for an application. Well, it looks like I was too restrictive which led to the error message in the title.
TL;DR
- When you publish an application via EntraID Appliction Proxy, the application is generated with a password credential valid for 1 year (actually 365 days + 4 minutes)
- if you have Workload Identites Premium licence* and have set the default password credential lifetime to 12 months or less, Entra ID will not be able to create the Application Proxy application resulting in this very informative error message upon application creation: ‘Application operation failed’
- Conclusion: when using passwordLifetime restiction in the defaultAppManagementPolicy and you intend to use AppProxy, make sure to set this lifetime to at least 366 days
Explained
When publishing a new application via Entra ID Application Proxy, I encountered this very detailed and error message: ‘Application operation failed’
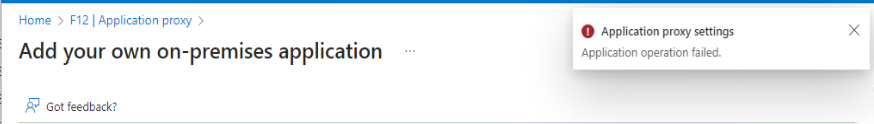
I went through some previously published applications to get an idea what may be wrong… And on the ‘Certificates & secrets’ page I had a flashback about configuring password credentials policy, then I was on the right track with a small surprise.
When an application is published with Application Proxy, an app registration is created with a password credential.
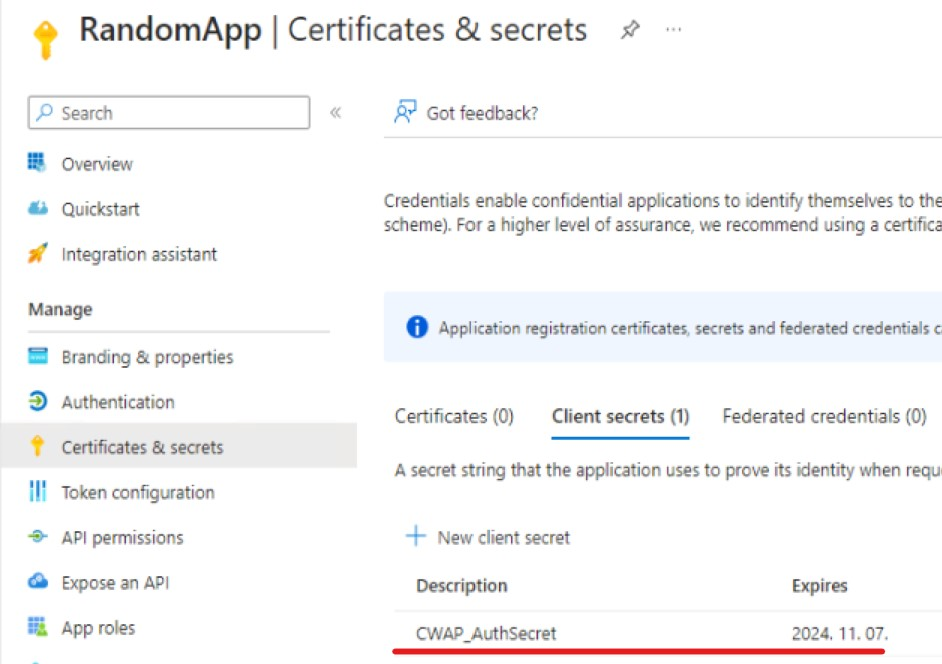
There is nothing you can do about it (as far as I know), you just live with it – it is handled by Microsoft automatically, I guess.
When you create a passwordLifetime policy specifying 12 months of lifetime, it is automatically translated to 365 days in the policy. On the next screenshot you can see my previous PATCH payload for defaultAppManagementPolicy which was followed by a GET to countercheck the settings:
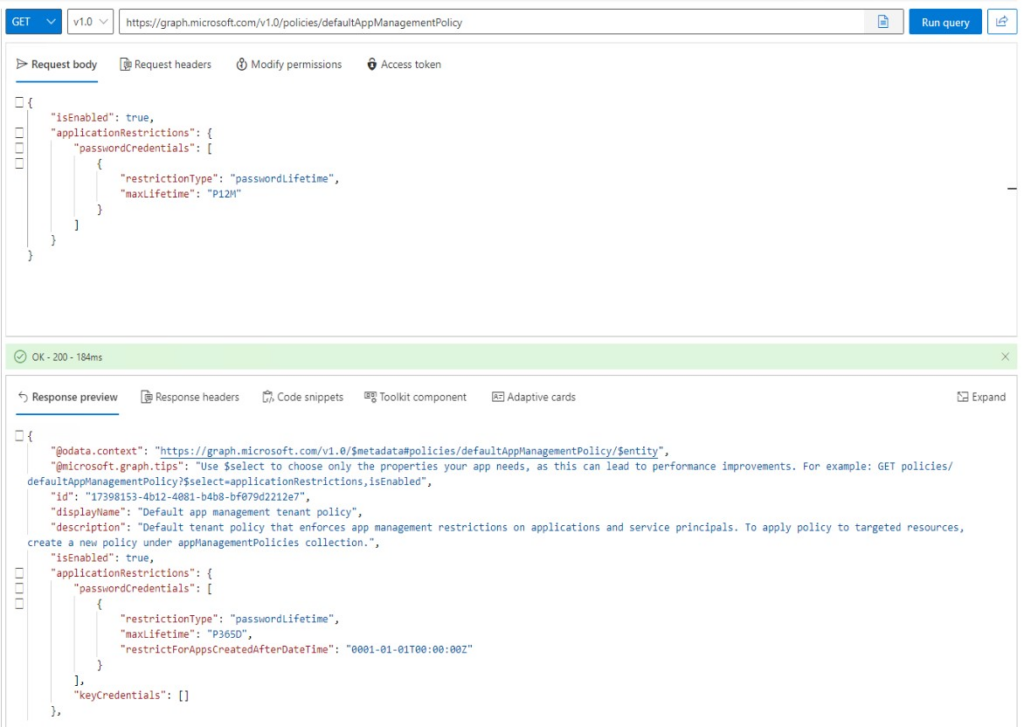
Remark: 12 months is not neccessarily 365 days (leap years!) This may cause issues in automations too when attempting to create a password valid for 1 year/12 months, which is 366 days in this case.
The point is that even if you set this lifetime to P12M (12 months) or P365D (365 days) this will prevent Application Proxy from adding the password credential, because the expiration for this password is set to T+365 days+4 minutes:
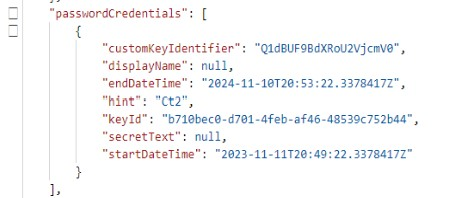
To get over this issue, modify the defaultAppManagementPolicy to allow 366 days of lifetime for a password credential:
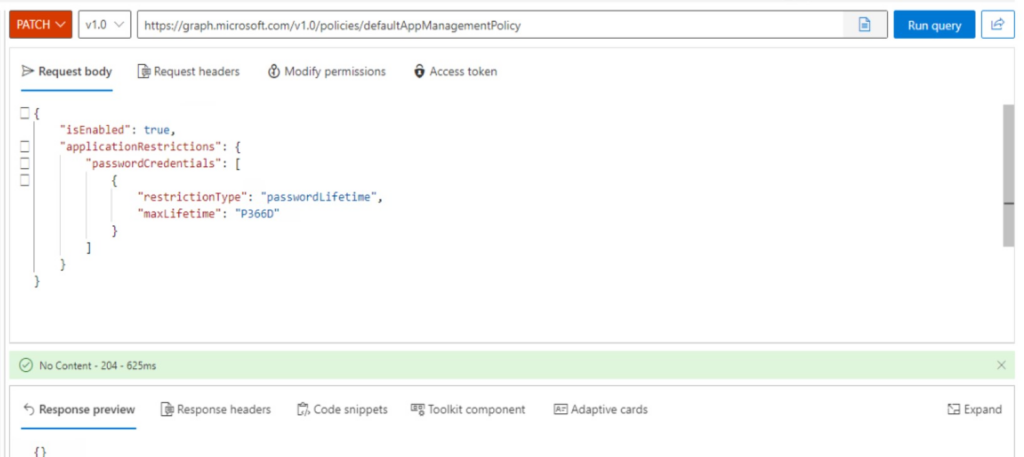
Now the application is successfully published:

*I used a trial licence back in those days to set up the policies…when the trial licence expires, these policies remain effective, but you will not be able to modify these settings – so you have to buy a licence to roll back these changes. So be cautious when playing with settings tied to a trial licence 🙃
