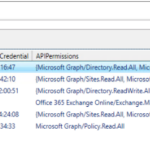
Recently I tried to set up ClaimXRay NG with the guidance of DSInternals, learned things, failed here and there and stumbled upon a totally-not-helpful error message: “There was an error in the uploading the private certificate and password. Please try again or contact support.” To cut to the chase: This message appeared when I was […]